Vulnerability Assessment
Stay ahead of potential threats with TTR Technology’s Vulnerability Assessment. Our vulnerability assessment service provides continuous scanning, analysis, and remediation of vulnerabilities, ensuring your systems are secure against evolving threats. Benefit from our fully-managed solution at a cost-effective price, offering top-tier protection without the overhead of hiring a dedicated security team.
Why Choose Us
- Certified with SOC 2 Type II and ISO 27001
- Industry Beating Priced Premium Quality Service
- 1000+ customers across 20+ countries
- Global Locations
- Fully-Managed Turnkey/Co-Managed Options
- 15-Min Gold SLA
- GDPR and Local Privacy Laws Compliant
Protect Against Threats with Advanced Vulnerability Management
- Vulnerability Management and Patch Management-as-a-Service from TTR Technology expertly handle the entire lifecycle of vulnerability assessment for your organization. Our service includes configuration, continuous scanning, detection, and prompt remediation of vulnerabilities, all managed efficiently. With our turnkey solution, you receive comprehensive security coverage at a cost starting lower than hiring a single security engineer. This ensures robust protection and proactive management, giving you peace of mind while keeping your systems secure and compliant.
Scan
Runs continuous scans to get visibility
Analyze
Analyzes systems for issues, risks, and threats
Detect
Detects deviations and changes as they occur
Remediate
Remediates detected flaws, risks, and threats
Automate
Automates end-to-end tasks
Prevent
Protect devices from potential breaches
24x7 Fully-Managed Vulnerability Management and Patch Management Service
- World’s largest built-in Vulnerability Database (160,000+ Checks).
- 24x7 Real-time Continuous Vulnerability Scans
- Vulnerability Scanning and Detection in less than 5 Minutes.
- Detected Vulnerability Validations and Prioritizations
- Deploy Patches on all Major OSs and 300+ Thirdparty Apps
- Integrated Patch Management Module to Remediate Vulnerabilities.
- Comply with Industry Benchmarks and Security Standards.
- Dedicated Vulnerability Scanning and Patch Remediation Team.
- Effortless Rollback for an Error-prone Software Patches.
On-Demand Vulnerability Management Scans for Network and IP Ranges
- Public/External Vulnerability Management Scans.
- Internal Vulnerability Scans.
- Web Application Vulnerability Management Scans.
- Discover unknown assets.
- Proactively identify and prioritize vulnerabilities.
- Scan Risk Scores and Prioritization.
- Custom Scan Result Reports.
- Vulnerability Remediation Recommendations.
- Diverse array of sensors.
- Credentialed/Non-Credentialed Scans.
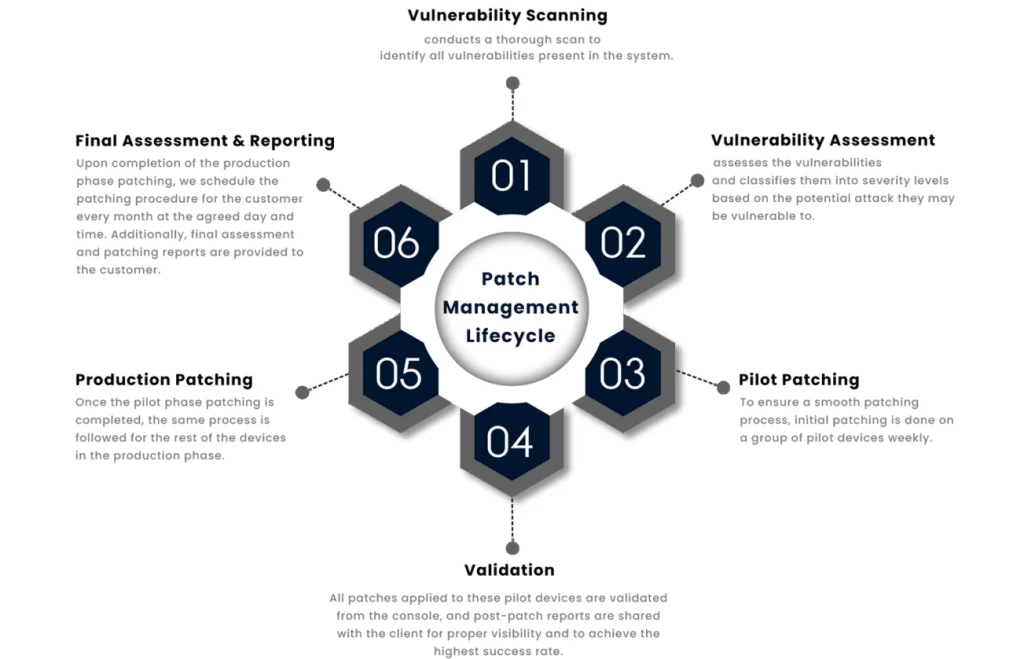
What MSP/MSSP and End Clients Get
- Fully Managed TurnkeyVulnerability Management and Patch Management Service.
- 24x7 Continuous vulnerability management.
- 24x7 Steady State Management of the VM and PM Products
- Industry Leading GOLD Service Level Agreements.
- Full Multi-Tenant Environment.
- Access to Customer Tenant Instances.
- Recurring Weekly and Monthly SOC Governance Calls
- Customized Incident Escalations.
- Assigned NamedVulnerability Management and Patch Management Engineers.
- Dedicated local 1800-SOC number.
Vulnerability Management and Patch Management Service Benefits
- Accelerate risk analysis to save valuable time.
- Continuous monitoring of evolving attack surface.
- Noise is suppressed & only True Positives are escalated - Customers don’t have to deal with overwhelming alerts and false positives.
- Customer gets full access to Vulnerability Management and Patch Management Multi-Tenant Instances.
- Customer gets access to SOC Ticketing Portal
- Vulnerability Management and Patch Management Engineers available to jump on Incident Containment Bridge Calls (No extra charges).
Let us assist with your project.
We're here to help!
Get a free consultation to see how Great Technical can elevate your business with tailored software solutions.
