With the increasing number of cyberattacks, companies have started investing more in protecting their digital information and systems. But the question is, how much should be spent?
This guide focuses on the major factors that help you about how to optimize cybersecurity budget breakdown. It will help you understand how resources can be allocated effectively to managed IT services for your businesses.
Why Cybersecurity Budgets Matter

Cybercrime costs are increasing day by day. It is expected that by 2027 it will cost the world over $23 trillion. The common cyber threats like phishing, ransomware, and data breaches are the most common types of cybercrimes. So it has become very important to put protective measures on your system for strong cyber security.
Ask yourself: Are you spending enough in your cybersecurity defenses for protect your business?
Why Do You Need to Consider Strong Cyber Security Measures?
- Geopolitical Risks: Due to geopolitical risk 71% of European information chief officers worry about cyber warfare.
- AI Factor: AI is making attacks faster and which is harder to detect and effecting industry majorly.
- Cloud Infrastructure: Managing security for all types of cloud platforms is tough. One mistake, can cost a high and things can quickly go wrong.
Cyber Threats You Can’t Ignore
- Ransomware Attacks: In 2023, The ransomware attacks payments hit a record $1.1 billion. That is a massive financial loss for the US industry.
- Social Engineering: 98% of all cyberattacks that consist up of few from social engineering. Even the best hacker breach the best defenses system.
- Data Breaches: Do you want to know the average cost of a data breach in 2023? Let me tell you. It was $4.45 million. Can your business afford that? I sure you never want.
- Regulatory Pressure: As we know hackers are adopting new ways to breach security, so besides existing regulations like GDPR and HIPAA, new rules are adding, including amendments to the FTC safeguard Rule . Staying compliant is not optional, it’s a necessity.
I’ve seen too many businesses think they’re safe, but actually they’re not. One attack can cost you millions and your peace of mind. The solution? Constantly upgrade your defenses system, stay informed, and act promptly before it’s too late.
Is your security keeping up? Or are you at risk?
Ask Yourself: Are You Spending Enough on Cybersecurity?
On average, businesses allocate about 12% of their IT budgets to cybersecurity, though this varies by industry due to differing risks and regulations. Let’s know about for each industry, problem, and solution for effective measure. Below are the Figure for cybersecurity across different industries
Cyber Security Budget Allocation By Sector
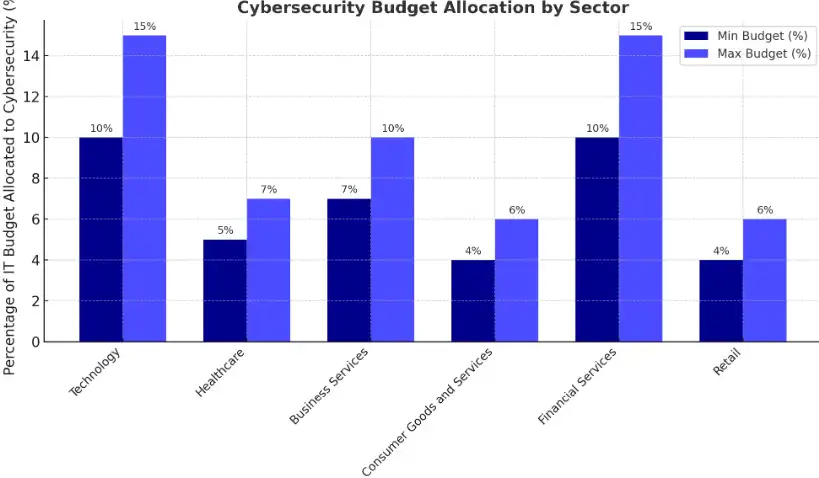
Technology:
- Problem: Tech companies handle sensitive data, which makes them targets for cyberattacks.
- Solution: They allocate about 10%–15% of their IT budget to cybersecurity.
Healthcare:
- Problem: Patient data is highly sensitive; that’s why the healthcare sector remains a vulnerable target.
- Solution: Most healthcare providers invest around 5%–7% of their IT budget on security.
Business Services:
- Problem: Business service providers deal with client data and operational systems, making them attractive to cybercriminals.
- Solution: Typically, they spend about 7%–10% of their IT budget on cybersecurity.
Consumer Goods and Services:
- Problem: Consumer-facing companies manage payment info and personal data, making them frequent targets of cyberattacks.
- Solution: These companies dedicate 4%–6% of their IT budget to security.
Financial Services:
- Problem: With a wealth of sensitive financial data, financial sectors are always at high risk.
- Solution: They allocate between 10%–15% of their IT budget to cybersecurity.
Retail:
- Problem: Retailers are frequent targets, especially due to payment and customer data.
- Solution: They allocate about 4%–6% of their IT budget to cybersecurity.
As cyber threats increase with the passage of time, assessing your cybersecurity budget is essential. Is your company’s budget aligned with these trends, or are you at risk of falling behind? Contact TTR Technology for a free consultation about the cyber security budget breakdown.
What is the Structure of a Cybersecurity Budget?

Let’s take a look at how a typical cybersecurity budget breakdown is structured.
1. Security Tools and Technology
If you want to have a strong cybersecurity plan, you need to invest in the right cybersecurity tools such as MDR, XDR, MDM, EDR, MFA and many more. These tools help in detecting and preventing potential threats.
Following are the key areas that need to be focused.
- Firewalls and Intrusion Detection Systems (IDS/IPS): The main function of firewalls is to keep a security check on the incoming and outgoing traffic. While detection systems are used to monitor traffic for any unusual activity.
- Antivirus and Anti-Malware Software: There are many software’s that detect and remove harmful malware from the system. Every company must have such software because, without it, your network is a very easy to breach for cybercriminals.
- Encryption Solutions: Encryption is the best way to protect sensitive data. Even if the data is accessed by an unauthorized person, it can not be view or decode without the encryption key.
- Multi-Factor Authentication (MFA): If you want to make it hard for hackers to gain access to your data then you should add an extra layer of security. Multi factor authentication gives that additional layer of security.
- Backup Solutions: Backup solutions are especially important to recover data when a mishap occurs. In case of a ransomware attack or accidental deletion, the data can be easily recovered.
Cost of Risk Without Tools: Data breaches could cost between $3.86 million and $8.64 million on average per incident, with firewalls and antivirus being the first line of defense.
Stats: In 2023, over 73% of cyberattacks targeted small businesses, many of which lacked these basic security tools. Stats: 2023 Business Impact Report
2. Employee Training and Awareness
It’s not always the technology that poses a risk to data security. Most systems are vulnerable due to mistakes done by humans. Human error accounts for almost 74% of data breaches every year. Errors usually involve social engineering, misuse and mistakes.
Here’s what you should include in your budget.
- Phishing Simulations: Create real world phishing scenarios to train your employees. Test their responses and raise awareness against these scams. This will greatly reduce the chances of success in actual attacks.
- Cybersecurity Training Programs: Your employees need training sessions to know about the latest cyber threats and how to identify them. Frequent training sessions ensure that employees have knowledge about new security practices.
- Incident Response: A cyber drill is used to test the actions of employees in case a cybersecurity incident occurs. It helps the employees to understand how to react when faced with a problem.
Cost of Risk Without Training: Human error leads to 74% of data breaches; lack of employee training can cost companies $1.5 million more per breach due to phishing and social engineering attacks.
Ask yourself: When was the last time your team had cybersecurity training? If it’s been a while, now’s the time to invest. Content TTR Technology for Cyber Security Awareness Training
3. Cybersecurity Personnel and Expertise
You always need skilled people for more complicated tasks. As cybersecurity is an important issue, you need to hire Managed IT services experts with professional IT skills to identify any cyber attack. But expertise always comes with a price. Their salaries may take a large portion of your budget.
Following is where your money will go.
- In-House Cybersecurity Staff: IT experts like cybersecurity analysts, security engineers, and a Chief Information Security Officer (CISO) are included in this category. They professionally monitor and maintain your security systems.
- Managed Security Services (MSS): The internal IT team may be more costly. It is always a good idea to outsource cybersecurity needs to managed IT services. They offer excellent services like 24/7 monitoring, vulnerability management, and incident response.
- Penetration Testing: As a test, try hiring external IT specialists to fake cyber attacks on your system. This will help identify your system’s flaws and weak points before hackers find them.
Cost of Risk Without Experts: Without skilled personnel, incident response times increase significantly, leading to losses of up to $2.5 million due to prolonged exposure to threats.
4. Compliance and Governance

Every business needs to stay compliant with the cybersecurity regulations. If you fail to follow the security standards and regulations you might have to face heavy fines. This will also affect your company’s reputation.
To stay compliant with security regulations, allocate a budget for the following.
- Regulatory Compliance Tools: These are the tools that help to ensure that your company follows the rules and regulations related to data protection and security.
- Audits: Regular audits are a means to determine whether your security systems are compliant with cybersecurity regulations like GDPR (General Data Protection Regulation) and SOX (Sarbanes-Oxley Act).
- Risk Management Solutions: Identify the weaknesses in your system. Allocate budget for tools that monitor and manage cybersecurity threats. This can save you from expensive disasters in the future.
Cost of Risk Without Compliance: Non-compliance with regulations like GDPR can result in fines up to €20 million or 4% of global turnover, whichever is higher. Stats: Penalties for Noncompliance
Know more about: How is Cyber Security Legislation Protecting Businesses from Cyber Risks?
5. Incident Response and Recovery
Even if you have the best defense system for your business, data breaches can still happen. To minimize the damage, you need to take prompt action. This is where incident response planning comes in handy.
Consider keeping a fixed cybersecurity budget for the following.
- Incident Response Plans: There should be documentation for who to notify, how to act quickly during a breach, and how to recover from it. This is necessary for every business to deal with data breaches.
- Forensic Services: To prevent data breaches in the future, experts always investigate the causes of a breach. This is necessary so that the gaps can be filled.
- Cyber Insurance: in case of data breaches and ransomware attacks, the financial losses are covered by cyber insurance.
Cost of Risk Without Incident Response: The average cost of a data breach without a response plan is $2 million higher than with one, mainly due to increased recovery time.
6. Security Monitoring and Analytics

Certain real time monitoring tools are necessary for detecting any suspicious activity leading to a data breach. Early threat detection can help save your company a complete breach.
The following should be on your list.
- Security Information and Event Management (SIEM): These tools are helpful in identifying threats as soon as possible.
- Threat Intelligence Services: Allocate a specific portion of your budget for threat intelligence services. They provide information about the latest cyber risks.
Cost of Risk Without Monitoring: Lack of early threat detection can victim to advanced persistent threats (APTs), which cost an organizations average of $1.6 million.
7. Physical Security
Physical security is as important as cybersecurity to secure your digital assets. Nothing can save your network if the hacker gains physical access to your networks.
You need to be careful about the following things:.
- Access Control Systems: Do not allow any unauthorized person in sensitive areas. This can be done by using keycards and biometrics.
- Data Center Security: surveillance cameras and intrusion detection systems can help secure your venue from any unauthorized personnel from entering. These physical security measures can protect your data centers.
Cost of Risk Without Physical Security: Physical breaches can result in theft of intellectual property or hardware, costing up to $500,000 per incident due to lost data and equipment.
How to Manage Cyber Risks with GRC Framework
Managing security for businesses is potential task. As we know that even one mistake could cost millions. That’s why you have to go for Governance, Risk, and Compliance (GRC) framework.
The Problem: Cyber Threats and Compliance Stress
Cyberattacks are increasing and for a new company to implement the standards like NIST or ISO feel difficult. One mistake could mean a costly breach or fines.
The Solution: Trusted Frameworks and Real-World Testing
I highly recommended adopting NIST standards for clear guidance and used the MITRE ATT&CK framework to deal cyber attacks. This approach can help you fix vulnerabilities before they become problems.
The Result: Stronger Defenses and Peace of Mind
With this strategy, You will not only meet compliance but also make strong, effective systems. You can identify issues early and secure from threats.
Quick Tip: Take Action Today
When was your last security test? Start with NIST guidelines and run some attack practices. Even small steps make a big difference. Need help? TTR Technology is there for you, together, we can find your peace of mind.
Smart Cybersecurity Budgeting: Invest Wisely, Protect Effectively

It is important to spend wisely for budget planning regarding cybersecurity. Cyberthreats are present around every corner. Your systems need the latest protective measures to prevent data breaches.
TTR Technology will help you to planned budget that allows businesses to effectively defend against these threats. This not only saves money but also the reputation of the company. Ready to strengthen your cybersecurity? Contact TTR Technology now for expert guidance and protection.