Security Operation Center (SOC) works for you 24x7
DETECT | TRIAGE | DEFEAT
Attackers never sleep and neither do we. We leverage Next-gen SIEM, AI, UBA and Threat Intel combined with an expert cybersecurity team to protect your business 24×7 at a starting price less than what it would take you to hire a single security operations center analyst.
What is SOC-as-a-Service? - Security Operations Center
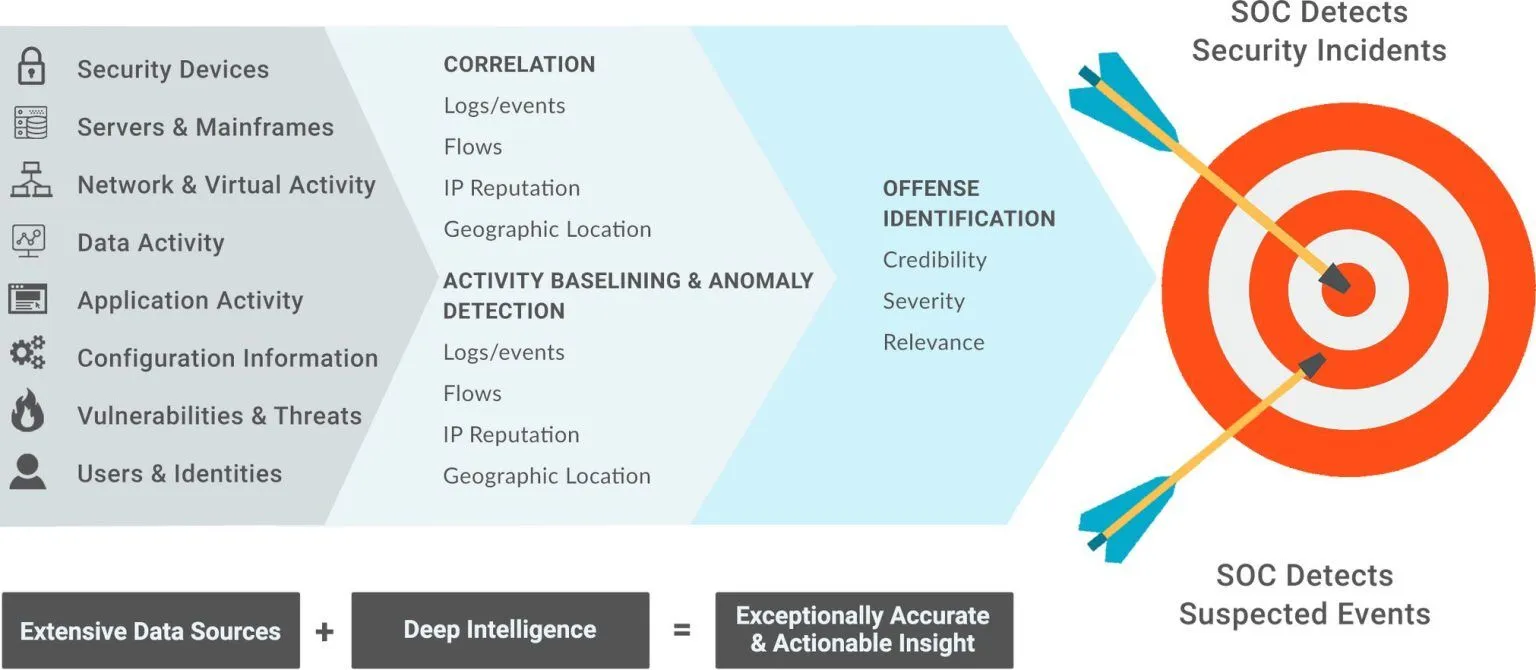
SOC-as-a-Service is a proactive Managed IT Solution which is designed to protect your business around the clock from cyber threat. By continuously monitoring your internal assets, endpoints, and cloud applications. The security solution detects potential cyber threats before they can cause damage. When an anomaly or breach is identified, expert cybersecurity analysts step in to investigate, providing you with detailed incident reports and actionable steps to resolve the issue. It’s like having a dedicated cybersecurity team that ensures your business stays secure without the complexity and cost of managing it in-house.
24/7 SOC Monitoring & Triage: Comprehensive Cybersecurity
- Monitor user behavior for threats using the MITRE ATT&CK Framework.
- Detect and manage malware, ransomware, and control server threats.
- Protect from phishing, misuse of privileges, and unauthorized access.
- Monitor suspicious activities, and policy violations.
- Track Indicators of Compromise and VPN access anomalies.
- Prevent data theft, block DoS/DDoS attacks, and detect unusual activities.
- Implement effective defense strategies and ensure privileged access security.
Supported Log Sources: Comprehensive Security Coverage
- Capture logs from server infrastructure and remote workstations.
- Monitor firewall and IDS systems for threats and breaches.
- Track domain controllers, email, and web proxies for protection.
- Integrate logs from antivirus and EDR for advanced threat detection.
- Include data from cloud and enterprise applications for a complete view.
- Support legacy applications and network devices like routers and switches.
- Extend coverage to DevOps environments for secure CI/CD.
Great Technical: Creating the New Standards of Success Through Creativity

What Managed Service Provider (MSP)
& Clients will Get?
- 24x7 Threat Detection, Analysis & Alert Triage
- Multi-Tenant Environment
- White-labeled Custom Reporting
- Weekly/Monthly SOC Reports
- Recurring SOC Governance Calls
- Access to Customer Data
- 750+ Custom Security Rules
- SOC Ticketing Portal Access
- Automation & Incident Response
- Customized SOC Escalations
- 30-min GOLD SLA
- 90-days to 1-year log Retention
- Assigned Named SOC Analysts
- Dedicated local 1800-SOC number
Security Operation Center (SOC) Service Benefits
- Customer’s network is monitored 24x7 by dedicated SOC analysts.
- Every detected alert is triaged, and custom incident report tickets manually created.
- Noise is filtered out, and only real issues are escalated, customers avoid dealing with false alerts.
- Too many alerts and inaccurate warnings.
- Customer gets full access to search SIEM ingested log data.
- Customer gets access to SOC Ticketing Portal
- 24x7 Real-time Incident Alerting & Triage by SOC
- SOC Analysts available to jump on Incident
- Containment Bridge Calls (No extra charges)
- 24x7 access to expert Named SOC analysts
Supported SIEM Products


Why Choose Us
- Certified with SOC 2 Type II and ISO 27001
- Premium service at competitive prices.
- Trusted by 1,000+ clients across 20+ countries.
- Global SOC locations for broad coverage.
- Fully-managed or co-managed service options.
- 15-minute Gold SLA and full GDPR compliance.
